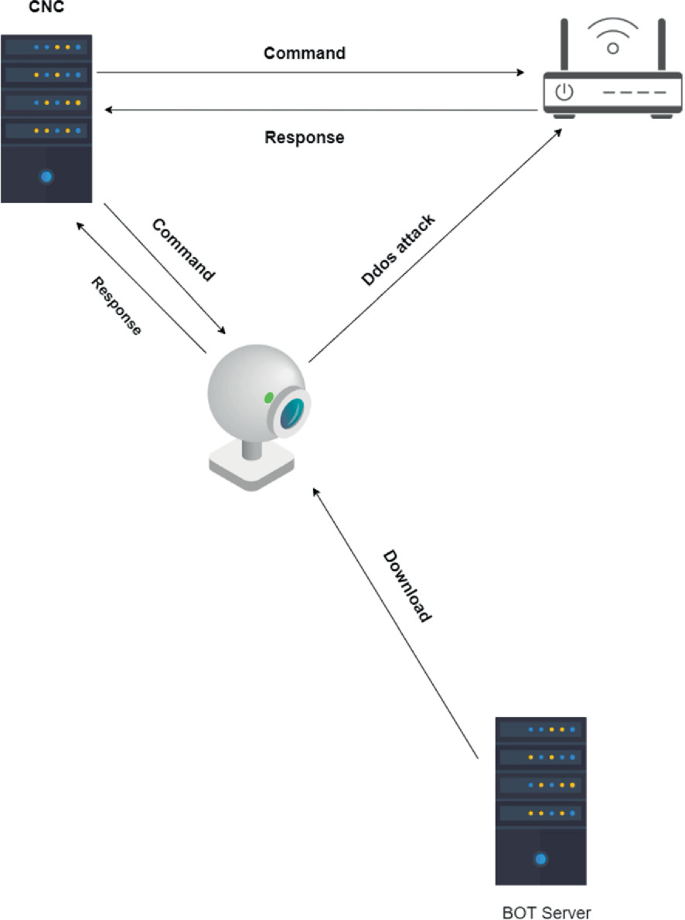
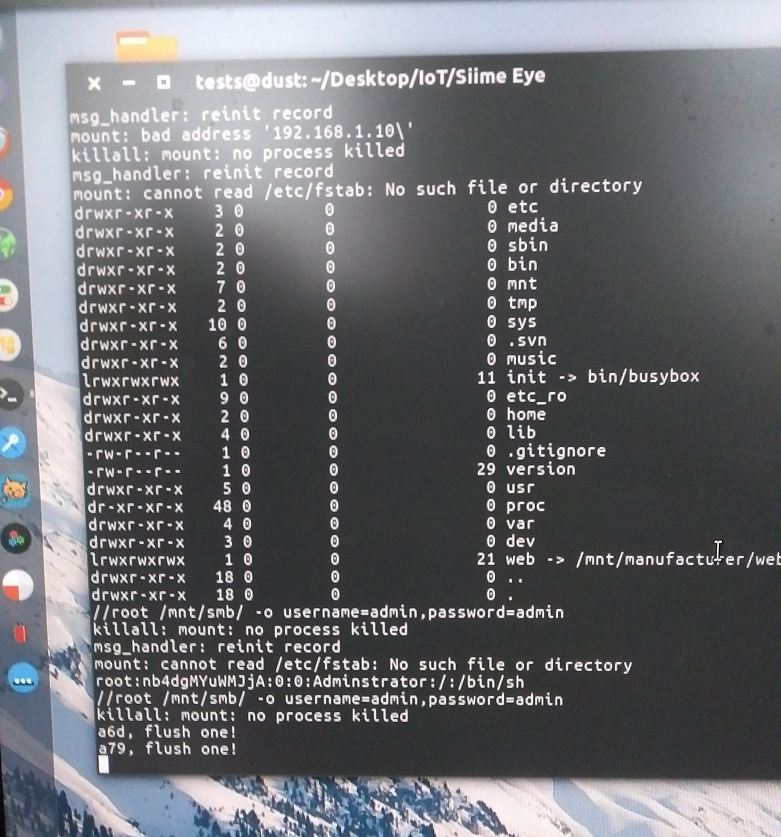
GitHub - jimywork/shodanwave: Shodanwave is a tool for exploring and obtaining information from Netwave IP Camera.
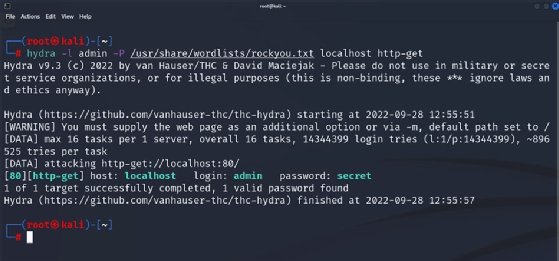
GitHub - prosecurity/wordlist-1: Collection of some common wordlists such as RDP password, user name list, ssh password wordlist for brute force. IP Cameras Default Passwords.

GigE Vision® Device IP Package (1GbE version/10GbE version) (Discontinued) - Semiconductor Business -Macnica,Inc.
GitHub - jeanphorn/wordlist: Collection of some common wordlists such as RDP password, user name list, ssh password wordlist for brute force. IP Cameras Default Passwords.

Information | Free Full-Text | A Comparison of Neural-Network-Based Intrusion Detection against Signature-Based Detection in IoT Networks

Applied Sciences | Free Full-Text | Design of OCC Indoor Positioning System Based on Flat Panel Light and Angle Sensor Assistance
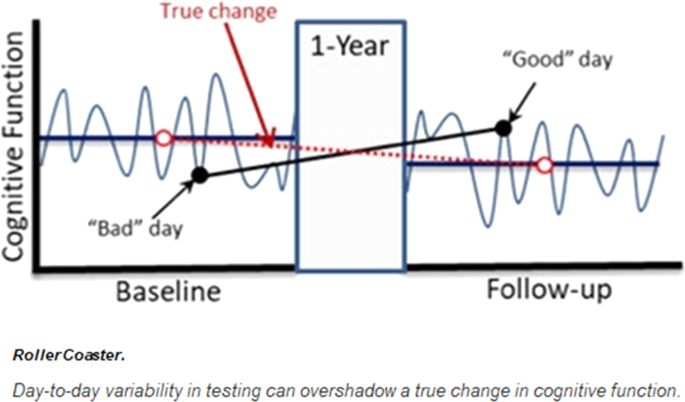
Using a Digital Neuro Signature to measure longitudinal individual-level change in Alzheimer's disease: the Altoida large cohort study | npj Digital Medicine
Frontiers | SSVEP BCI and Eye Tracking Use by Individuals With Late-Stage ALS and Visual Impairments








/Academy-The-top-password-cracking-techniques-used-by-hackers-Hero.jpg?width=1200&name=Academy-The-top-password-cracking-techniques-used-by-hackers-Hero.jpg)